Picture this: you’re managing a fleet of IoT devices spread across the globe, and you need a secure way to access them remotely. Enter RemoteIoT SSH AWS Example, your go-to solution for establishing rock-solid connections in the cloud. Whether you’re a seasoned developer or just starting out, this guide will walk you through everything you need to know about setting up SSH connections for IoT devices using AWS. No fluff, just actionable insights!
When it comes to IoT security, you can’t afford to cut corners. That’s why RemoteIoT SSH AWS Example is such a game-changer. It combines the power of AWS’s cloud infrastructure with the reliability of SSH to give you peace of mind. From setting up your environment to troubleshooting common issues, this article has got you covered.
So, buckle up because we’re about to dive deep into the world of IoT and AWS. By the end of this guide, you’ll have the knowledge and tools to set up a secure, scalable, and efficient remote IoT system. Ready to level up your IoT game? Let’s get started!
Read also:Jillian Fink A Rising Star In The Spotlight
Table of Contents
- What is RemoteIoT SSH AWS Example?
- Why Use AWS for RemoteIoT?
- Setting Up Your AWS Environment
- Configuring SSH for RemoteIoT
- Securing Your IoT Devices
- Common Issues and Solutions
- Scaling Your RemoteIoT System
- Best Practices for RemoteIoT
- Real-World Examples
- Conclusion and Next Steps
What is RemoteIoT SSH AWS Example?
Let’s break it down, shall we? RemoteIoT SSH AWS Example refers to the process of setting up secure connections between your IoT devices and AWS using SSH. SSH, or Secure Shell, is a protocol that encrypts data transmitted between devices, ensuring that your communication remains private and protected.
For IoT enthusiasts, this setup is crucial because it allows you to remotely manage and monitor your devices without compromising security. AWS, being one of the most robust cloud platforms out there, provides the infrastructure needed to scale your IoT projects seamlessly.
In simple terms, RemoteIoT SSH AWS Example is like having a virtual fortress for your IoT devices. You get the best of both worlds: the security of SSH and the scalability of AWS.
Why SSH Matters in IoT
SSH isn’t just another acronym; it’s a lifeline for IoT security. Here’s why:
- Encryption: SSH encrypts all data transmitted between your device and server, making it nearly impossible for hackers to intercept sensitive information.
- Authentication: SSH ensures that only authorized users can access your devices, adding an extra layer of security.
- Reliability: With SSH, you can establish stable and consistent connections, even in challenging network conditions.
Why Use AWS for RemoteIoT?
AWS is the go-to platform for IoT projects for a reason. It offers a wide range of services tailored specifically for IoT, making it easier to manage and scale your devices. Here are a few reasons why AWS is the perfect fit for RemoteIoT:
First off, AWS provides a secure and scalable environment for your IoT devices. With features like AWS IoT Core, you can easily connect, monitor, and manage millions of devices. Plus, AWS’s global infrastructure ensures that your devices remain accessible from anywhere in the world.
Read also:Oxleak The Untold Story You Need To Know About
Another advantage of AWS is its integration capabilities. You can seamlessly integrate SSH with other AWS services, such as Lambda and S3, to create a powerful ecosystem for your IoT projects. And let’s not forget about AWS’s robust security features, which are designed to protect your data at every level.
Top AWS Services for IoT
Here are some AWS services that you’ll want to explore for your RemoteIoT project:
- AWS IoT Core: A managed cloud service that lets you connect and interact with IoT devices.
- AWS Lambda: Run code in response to events without provisioning or managing servers.
- Amazon S3: Store and retrieve data for your IoT applications.
- AWS CloudWatch: Monitor your IoT devices and applications in real-time.
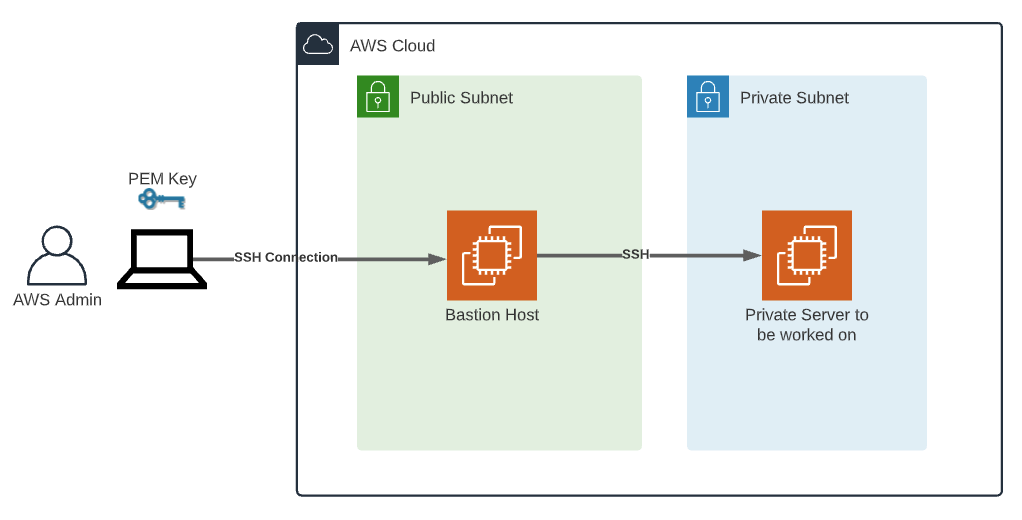
Setting Up Your AWS Environment
Alright, let’s get our hands dirty and set up your AWS environment for RemoteIoT. The first step is to create an AWS account if you don’t already have one. Once you’re logged in, follow these steps:
- Go to the AWS Management Console and navigate to AWS IoT Core.
- Create a new thing by clicking on the “Register a thing” button.
- Download the generated certificate and private key; you’ll need them later for authentication.
- Set up policies to define what actions your device can perform.
Don’t forget to configure your VPC (Virtual Private Cloud) to ensure secure communication between your devices and AWS. This step is crucial for maintaining the integrity of your IoT system.
Pro Tip: Use AWS CloudFormation
For those who want to automate the setup process, AWS CloudFormation is your best friend. It allows you to define your infrastructure as code, making it easier to replicate and manage your environment.
Configuring SSH for RemoteIoT
Now that your AWS environment is ready, it’s time to configure SSH for your IoT devices. Here’s how you can do it:
First, install an SSH server on your IoT device. Most Linux-based devices come with OpenSSH pre-installed, so you might not need to do much here. If not, you can install it using the following command:
sudo apt-get install openssh-server
Next, generate an SSH key pair on your local machine:
ssh-keygen -t rsa -b 4096 -C "your_email@example.com"
Once you have your key pair, copy the public key to your IoT device:
ssh-copy-id user@your-iot-device
Enhancing SSH Security
While SSH is secure by default, there are a few steps you can take to enhance its security:
- Disable password authentication and rely solely on key-based authentication.
- Change the default SSH port (usually 22) to something less obvious.
- Set up a firewall to restrict access to your SSH server.
Securing Your IoT Devices
Security should always be at the forefront of your IoT strategy. Here are some best practices to keep your devices safe:
Start by updating your firmware regularly. Manufacturers frequently release updates to patch security vulnerabilities, so staying up-to-date is crucial. Additionally, use strong passwords and enable two-factor authentication whenever possible.
Another important step is to segment your network. By isolating your IoT devices from your main network, you reduce the risk of a breach spreading to other parts of your system. And don’t forget to monitor your devices for suspicious activity using tools like AWS CloudWatch.
Common Security Threats in IoT
Here are some security threats you should be aware of:
- DDoS attacks: Hackers can use compromised IoT devices to launch massive attacks on your network.
- Malware: Devices with weak security measures can become infected with malicious software.
- Data breaches: Sensitive information can be stolen if your devices aren’t properly secured.
Common Issues and Solutions
Even the best-laid plans can encounter hiccups. Here are some common issues you might face when working with RemoteIoT SSH AWS Example and how to solve them:
Problem: Unable to connect to your IoT device via SSH.
Solution: Check your firewall settings and ensure that the SSH port is open. Also, verify that your device is connected to the internet.
Problem: Slow connection speeds.
Solution: Optimize your network configuration and consider using AWS’s global infrastructure to reduce latency.
Problem: Authentication failures.
Solution: Double-check your SSH keys and ensure that they match on both your local machine and IoT device.
Scaling Your RemoteIoT System
As your IoT project grows, you’ll need to scale your system to accommodate more devices. AWS makes this process seamless with its auto-scaling capabilities.
With AWS Auto Scaling, you can automatically adjust the number of devices based on demand. This ensures that your system remains efficient and cost-effective, even as your project expands.
Another scaling strategy is to use AWS IoT Greengrass, which allows you to run local compute, messaging, and data caching for your devices. This reduces the need for constant cloud connectivity, making your system more resilient.
Best Practices for RemoteIoT
Here are some best practices to keep in mind when working with RemoteIoT SSH AWS Example:
- Document everything: Keep detailed records of your setup and configuration for future reference.
- Test thoroughly: Before deploying your system, test it in a controlled environment to ensure everything works as expected.
- Monitor continuously: Use tools like AWS CloudWatch to keep an eye on your devices and address issues before they escalate.
Real-World Examples
To give you a better idea of how RemoteIoT SSH AWS Example works in practice, here are a couple of real-world examples:
Example 1: A manufacturing company uses RemoteIoT SSH AWS Example to monitor and control their production line remotely. By leveraging AWS’s IoT services, they’ve been able to reduce downtime and improve efficiency.
Example 2: A smart city initiative uses RemoteIoT SSH AWS Example to manage a network of sensors that monitor air quality, traffic patterns, and energy consumption. The system provides valuable insights that help city planners make data-driven decisions.
Conclusion and Next Steps
And there you have it, folks! RemoteIoT SSH AWS Example is your key to unlocking the full potential of IoT in the cloud. By following the steps outlined in this guide, you can set up a secure, scalable, and efficient system that meets your needs.
Remember, security should always be your top priority. Stay vigilant, keep your devices updated, and monitor them closely for any signs of trouble. And if you ever get stuck, don’t hesitate to reach out to the AWS community for support.
So, what are you waiting for? Start experimenting with RemoteIoT SSH AWS Example today and take your IoT projects to the next level. And don’t forget to share your experiences in the comments below or explore other articles on our site for more IoT tips and tricks. Happy tinkering!